Forging Fortress in the Clouds: A Deep Dive into Cloud Security Architecture
Understand the fundamental principles, essential components, and strategic models required to build an impenetrable digital infrastructure in any cloud environment.
Are your cloud environments truly secure against the ever-evolving array of digital threats, or are hidden vulnerabilities leaving your critical data exposed?
Imagine designing a robust, resilient digital fortress where your data is protected by layers of intelligent defense, even as your infrastructure scales and evolves.
Discover how to build a robust cloud security architecture, transforming potential weaknesses into formidable strengths that safeguard your entire digital future.
The relentless march of digital transformation has seen businesses of all sizes flock to the cloud, drawn by the promise of scalability, flexibility, and reduced operational overhead. This rapid shift to cloud computing, however, introduces a complex new frontier for cybersecurity. While cloud providers offer a secure foundation, the ultimate responsibility for data protection and security within those environments often rests squarely on the client. Without a deliberate and well-executed strategy, the very advantages of cloud adoption can become sources of unforeseen vulnerability.
This is precisely where Cloud Security Architecture becomes paramount. Far from a mere checklist of security tools, it represents a comprehensive framework of strategies, policies, and technologies meticulously designed to protect your cloud assets, applications, and data. It's about designing a resilient and secure cloud computing architecture from the ground up, one that anticipates threats and builds in layers of defense. This guide explores the foundational principles, essential components, common models, and best practices for developing and implementing a robust cloud security architecture, ensuring your digital infrastructure remains robust, compliant, and ready for tomorrow's challenges.
Quick navigation
- Defining Cloud Security Architecture: Foundations for the Future
- Core Principles of Secure Cloud Design
- Key Components: Building Blocks of Cloud Security Architecture
- What this means for you
- Architectural Models and Best Practices Across Cloud Environments
- Risks, trade-offs, and blind spots
- Main points
Defining Cloud Security Architecture: Foundations for the Future
Cloud Security Architecture isn't a single product or a one-time setup; it's a dynamic, evolving discipline that encompasses the entire lifecycle of cloud deployment, from initial design to ongoing operations. It’s the meticulous planning, implementation, and continuous refinement of security controls and processes within a cloud environment to protect data, applications, and infrastructure from cyber threats. But why is this fundamentally different from securing traditional on-premise infrastructure?

The distinctions are significant. Firstly, the Shared Responsibility Model is central to cloud security. Cloud providers (like AWS, Azure, Google Cloud) are responsible for the security *of* the cloud (the underlying infrastructure), while the customer is responsible for security *in* the cloud (their data, applications, operating systems, and network configurations). Misunderstanding this shared boundary is a common vulnerability. Secondly, the ephemeral and distributed nature of cloud resources, with instances spinning up and down rapidly across multiple regions, demands a security approach that is equally agile and scalable. Traditional perimeter-based security often falls short in such dynamic environments. Finally, in the cloud, identity becomes the new perimeter. With decentralized access and diverse endpoints, strong Identity and Access Management (IAM) is no longer just a component but a foundational pillar of defense.
The key objectives of a robust cloud security architecture are clear: ensuring data confidentiality, integrity, and availability (CIA triad). This means protecting sensitive information from unauthorized access, ensuring its accuracy and completeness, and guaranteeing that authorized users can access it when needed. Beyond the CIA triad, a strong architecture also aims for regulatory compliance across various industry and regional standards (e.g., GDPR, HIPAA, PCI DSS) and builds operational resilience, allowing the organization to withstand and recover quickly from security incidents. A well-designed cloud security architecture, therefore, doesn't just bolt security onto an existing cloud computing architecture; it integrates security as an inherent, fundamental aspect of every design decision. How can you ensure your architectural decisions aren't just efficient, but inherently secure?
Core Principles of Secure Cloud Design
Building a resilient cloud security architecture requires adherence to a set of core principles that guide design and implementation. These aren't mere suggestions but foundational tenets that strengthen your defenses against a constantly evolving threat landscape. Ignoring even one can introduce significant vulnerabilities, no matter how sophisticated your tools.
The principle of Zero Trust stands at the forefront: "never trust, always verify." This means no user, device, or application is inherently trusted, regardless of whether it's inside or outside the network perimeter. Every access request must be authenticated, authorized, and continuously validated. Closely related is the principle of Least Privilege, which dictates that users and systems should only be granted the minimum necessary permissions to perform their tasks. This drastically limits the potential damage if an account is compromised. Imagine a key that only opens one specific door, rather than a master key to the entire building; that’s least privilege in action.
Defense in Depth is another critical concept, advocating for a layered security approach. Instead of relying on a single security control, multiple overlapping safeguards are deployed. If one layer is breached, others are still in place to protect the asset. Think of a castle with multiple walls, moats, and guards – each layer providing additional protection. Continuous Monitoring provides real-time visibility into your cloud environment, detecting suspicious activities and potential threats as they emerge. This involves collecting and analyzing logs, metrics, and network traffic, enabling rapid response to incidents.
Automation plays a vital role in cloud security, reducing human error and accelerating security processes. From automated vulnerability scanning to orchestrated incident response playbooks, automation ensures consistent application of policies and frees security teams to focus on more complex challenges. Finally, Data Protection is paramount. This includes implementing encryption for data both at rest (stored on disks) and in transit (moving across networks), alongside robust Data Loss Prevention (DLP) strategies to prevent sensitive information from leaving controlled environments. Coupled with these, a clear understanding of the Shared Responsibility Model helps clarify which security tasks are handled by the cloud provider and which remain yours, preventing critical security gaps. Are you building these foundational principles into every aspect of your cloud strategy, or are you leaving gaps that attackers can exploit?
Key Components: Building Blocks of Cloud Security Architecture
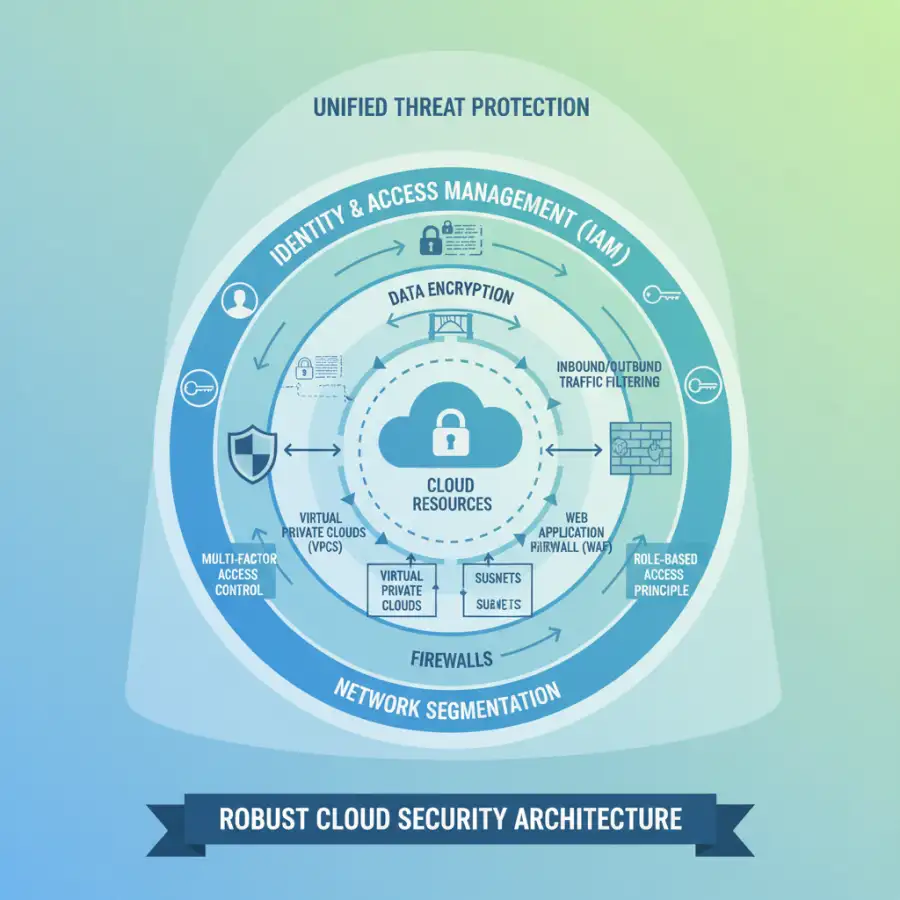
To translate principles into practice, cloud security architecture relies on a suite of interconnected components, each addressing specific facets of protection. These building blocks are essential for constructing a comprehensive and resilient defense across your cloud infrastructure.
Identity and Access Management (IAM) forms the bedrock. It's about authenticating users and services, then authorizing their access to cloud resources based on their roles and policies. This includes implementing Multi-Factor Authentication (MFA), Single Sign-On (SSO), and granular, context-aware permissions. Robust IAM ensures that only authorized entities can access your sensitive data. Next, Network Security defines how traffic flows within and to your cloud environments. This involves Virtual Private Clouds (VPCs) for network isolation, security groups and Network Access Control Lists (NACLs) for granular traffic filtering, cloud firewalls, Web Application Firewalls (WAFs) to protect against common web exploits, and Distributed Denial of Service (DDoS) protection to maintain availability.
Data Security focuses directly on your most valuable asset: information. This means pervasive encryption for data at rest (e.g., encrypted databases and storage buckets) and in transit (e.g., TLS/SSL for network communications). Data classification, tokenization, and Data Loss Prevention (DLP) solutions are also crucial to identify, monitor, and protect sensitive data wherever it resides. Endpoint Security extends protection to individual virtual machines, containers, and serverless functions. Cloud Workload Protection Platforms (CWPP) and host-based Intrusion Detection/Prevention Systems (IDS/IPS) monitor for malicious activity at the workload level.

Security Information and Event Management (SIEM) and Cloud Security Posture Management (CSPM) tools provide the necessary visibility and intelligence. SIEMs aggregate logs and events from across your cloud environment for analysis and alert generation, while CSPM tools continuously assess your cloud configurations against best practices and compliance benchmarks, identifying misconfigurations and compliance deviations. Finally, with the rise of modern development practices, Container Security (for Docker, Kubernetes) and API Security (protecting the interfaces through which applications communicate) have become indispensable components, ensuring that even the newest technologies are secured from their inception. Are you utilizing each of these crucial building blocks to create a truly holistic defense?
What this means for you
Understanding and implementing a robust Cloud Security Architecture isn't just an academic exercise; it has profound, practical implications for both businesses and individual IT professionals. The benefits extend far beyond merely avoiding breaches, impacting everything from regulatory standing to innovation velocity.
For Businesses, the advantages are multifaceted. Foremost is enhanced data protection. A well-architected cloud security framework minimizes the risk of data breaches, ensuring the confidentiality and integrity of your most sensitive information. This directly contributes to maintaining customer trust and protecting your brand reputation. Secondly, it ensures robust regulatory compliance. With evolving regulations like GDPR, HIPAA, and PCI DSS, a strong cloud security architecture helps organizations meet stringent compliance requirements, mitigating the risk of hefty fines and legal ramifications. This proactive approach saves significant resources compared to reacting to compliance failures.
Beyond compliance, businesses gain reduced risk of breaches and the associated financial and reputational damage. The cost of a data breach can be astronomical, encompassing legal fees, notification expenses, forensics, and lost business. A secure architecture acts as a preventative measure, offering significant long-term cost savings. In fact, a thorough ROI analysis often reveals substantial returns on investments in advanced security measures. Furthermore, it fosters operational resilience, meaning your business can quickly recover from any security incidents, minimizing downtime and ensuring business continuity. Ultimately, a secure cloud environment empowers businesses to embrace new technologies and expand operations with confidence, enabling faster innovation without compromising safety. Does your current security posture enable innovation, or does it stifle it?
For IT Professionals, mastering Cloud Security Architecture translates into a clear roadmap for securing modern deployments. It provides the knowledge and skills to design, implement, and manage secure cloud environments effectively. This expertise is in incredibly high demand, offering significant opportunities for professional growth and career advancement in a field that is constantly expanding. Being able to architect scalable, secure cloud solutions positions you as a critical asset within any organization navigating the complexities of the digital landscape.
Architectural Models and Best Practices Across Cloud Environments
The beauty and complexity of cloud security architecture lie in its adaptability across various cloud service models and deployment types. Whether you're operating within Infrastructure as a Service (IaaS), Platform as a Service (PaaS), Software as a Service (SaaS), or a hybrid/multi-cloud environment, distinct architectural considerations and best practices apply. Recognizing these nuances is critical for deploying effective security controls.
In an IaaS (Infrastructure as a Service) model, you manage virtual machines, networks, and storage, giving you significant control but also greater responsibility. Best practices here include robust VM hardening, diligent operating system patching, effective network segmentation using VPCs, security groups, and network firewalls, alongside strong IAM policies for administrative access. The security of the underlying hypervisor and physical infrastructure remains the cloud provider's responsibility, but everything above that layer is yours to secure.
For PaaS (Platform as a Service), the cloud provider manages the underlying infrastructure and operating system, allowing you to focus on application development. Security best practices shift to emphasize application security, including secure coding practices, regular Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST), robust API security measures, comprehensive data encryption within the application layer, and thorough input validation to prevent common web vulnerabilities. While the platform itself is managed, your application's code and configuration are your primary security concern.
With SaaS (Software as a Service), the cloud provider manages virtually everything, from infrastructure to application. Your security responsibilities primarily revolve around secure configuration of the SaaS application itself, strong IAM controls for user access, vigilant vendor assessment to ensure the provider meets your security requirements, and defining clear data access policies. Mastering the secure configuration of these platforms, much like mastering Sage Intacct SaaS for accounting, is paramount to deriving full value without introducing unnecessary risk. For Hybrid and Multi-Cloud Security, the challenge lies in maintaining consistency of security policy and achieving unified visibility across diverse environments. Best practices involve implementing a centralized identity management solution, utilizing cloud-agnostic security tools where possible, and establishing a unified security management plane. Can your security strategy adapt seamlessly as your applications move between on-premise, public, and private clouds?
Finally, the integration of DevSecOps is a best practice that transcends all models. This involves "shifting security left" – integrating security considerations and controls throughout the entire software development lifecycle (SDLC), from design and coding to testing and deployment. By embedding security early and often into CI/CD pipelines, vulnerabilities are identified and remediated much earlier, reducing cost and risk.
Risks, trade-offs, and blind spots
Even with the most meticulously planned Cloud Security Architecture, inherent risks, trade-offs, and potential blind spots can emerge. Acknowledging these challenges is not a sign of weakness, but a crucial step towards building a truly resilient and adaptable defense. Understanding where vulnerabilities might lie allows for proactive mitigation strategies rather than reactive damage control.
One prevalent risk is Configuration Drift, where security settings and policies become inconsistent across environments due to manual changes, rushed deployments, or a lack of automation. This can create unintended security gaps, leaving parts of your infrastructure exposed. Closely related is the peril of Shadow IT, where employees or departments deploy unauthorized cloud services without IT oversight, bypassing established security controls entirely. This uncontrolled adoption creates significant blind spots and introduces unknown risks into the corporate network.
The sheer Complexity of managing multiple cloud environments, often coupled with diverse security tools, can overwhelm even experienced teams. Integrating various platforms, dashboards, and alerts can lead to alert fatigue and missed critical events. Another significant trade-off is Vendor Lock-in. Deep integration with a specific cloud provider's security services, while convenient, can make it difficult and costly to switch providers in the future, limiting your flexibility and negotiation power. This consideration is particularly relevant for businesses heavily invested in specific SaaS platforms, much like the commitment to a comprehensive SaaS accounting service which, once implemented, can be challenging to transition away from.
A persistent challenge is the Skill Gap. The rapid evolution of cloud technologies means many organizations struggle to find and retain cybersecurity professionals with the specialized knowledge required to secure complex cloud environments. This lack of in-house expertise can lead to misconfigurations, overlooked vulnerabilities, and inefficient incident response. Furthermore, Cost Overruns can occur if cloud security solutions are not carefully planned and optimized. While cloud promises cost efficiency, runaway consumption of security services or failure to properly manage resources can lead to unforeseen expenses. Finally, Compliance Misinterpretation is a common blind spot. Simply having the right tools isn't enough; understanding how specific controls map to regulatory requirements is crucial, and misinterpreting these obligations can lead to non-compliance despite significant security investments. Are you actively identifying and addressing these potential pitfalls, or are you hoping they simply won't materialize?
Main points
- Strategic Imperative: Cloud Security Architecture is fundamental for protecting digital assets in dynamic cloud environments, moving beyond traditional on-premise security models.
- Shared Responsibility: Always remember the shared responsibility model, clearly distinguishing between the cloud provider's security *of* the cloud and your organization's security *in* the cloud.
- Core Principles Guide Design: Implement Zero Trust, Least Privilege, Defense in Depth, Continuous Monitoring, Automation, and robust Data Protection as foundational design tenets.
- Comprehensive Components: Utilize key building blocks like IAM, Network Security, Data Security, Endpoint Security, SIEM/CSPM, Container Security, and API Security to build a layered defense.
- Tailored for Environments: Adapt your architectural approach based on the cloud service model (IaaS, PaaS, SaaS) and deployment type (hybrid/multi-cloud), integrating DevSecOps where applicable.
- Business and Professional Impact: A strong architecture leads to enhanced data protection, compliance, reduced risk, operational resilience for businesses, and significant career growth for IT professionals.
- Address Risks Proactively: Be aware of configuration drift, Shadow IT, complexity, vendor lock-in, skill gaps, and potential cost overruns, and plan mitigation strategies accordingly.
Evaluate your current cloud security posture and commit to architecting a resilient, adaptable framework that can protect your organization's most vital assets as you continue to innovate in the cloud.

