Fortifying the Digital Frontier: A Comprehensive Guide to Cloud Security
Understanding Principles, Best Practices, and Strategic Considerations Across Leading Cloud Platforms
In an era where digital transformation is no longer optional but essential, is your organization truly equipped to defend its valuable assets and sensitive data against the ever-evolving threats lurking in the cloud? The promise of agility and scalability comes with inherent complexities.
Navigating the intricate landscape of cloud platforms, shared responsibility models, and myriad security tools can feel like a daunting task, leaving many wondering where to begin in building a truly resilient cloud defense.
This comprehensive guide cuts through the noise, offering a deep understanding of cloud security principles, best practices, and strategic considerations across leading providers like Google Cloud and AWS, empowering you to forge an unyielding digital frontier.
The migration to cloud computing has fundamentally reshaped the technological landscape, offering unparalleled agility, scalability, and cost efficiency. However, with the boundless opportunities of the cloud comes a new frontier of security challenges. **Cloud security** is no longer a niche concern but a foundational imperative for any organization leveraging cloud infrastructure, platforms, or software. It encompasses a vast array of technologies, policies, controls, and services designed to protect cloud-based data, applications, and infrastructure from cyber threats. This includes everything from safeguarding servers and virtual machines to ensuring the integrity of stored cloud data security and managing access to cloud resources.
At its core, cloud security operates under a shared responsibility model, a critical concept distinguishing it from traditional on-premises security. Cloud providers (like Amazon Web Services and Google Cloud) are responsible for the security *of* the cloud, meaning the underlying infrastructure, while customers are responsible for security *in* the cloud, pertaining to their data, applications, and configurations. Misunderstandings of this model are a leading cause of cloud breaches. This comprehensive guide aims to thoroughly demystify cloud security, providing a deep understanding of its definition, core principles, essential components, and best practices across leading cloud platforms. Our goal is to equip you with a robust educational resource, offering strategic insights and a roadmap for building and maintaining an effective cloud security posture, ensuring your digital assets remain fortified against an increasingly sophisticated threat landscape.
Quick navigation
- The Cloud Imperative: Understanding the Modern Security Landscape
- Architecting Trust: Core Principles and Pillars of Cloud Security
- Layers of Defense: Key Components of a Comprehensive Cloud Security Strategy
- Best Practices in Action: Securing Your Journey Across Google Cloud and AWS
- What this means for you
- Risks, trade-offs, and blind spots
- Main points
The Cloud Imperative: Understanding the Modern Security Landscape
The journey into cloud computing is no longer a tentative exploration but a full-scale migration for businesses of all sizes. From infrastructure-as-a-Service (IaaS) and platform-as-a-Service (PaaS) to software-as-a-Service (SaaS), cloud models offer unparalleled flexibility, rapid deployment, and cost efficiencies. Yet, this transformative power introduces a paradigm shift in how we approach security. The traditional perimeter-based defenses designed for on-premises environments are simply inadequate for the dynamic, distributed nature of the cloud. The sheer scale, shared infrastructure, and API-driven accessibility of cloud environments present unique challenges that demand a specialized approach to **cloud security**.

The modern threat landscape is characterized by its constant evolution and increasing sophistication. Cloud environments, with their vast attack surface, are prime targets for a wide array of cyber threats, including data breaches, misconfigurations, account hijacking, API vulnerabilities, and denial-of-service attacks. The consequences of a cloud breach can be catastrophic: financial penalties, regulatory fines, severe reputational damage, and significant operational disruption. Furthermore, the inherent agility of the cloud, while a benefit, also means that misconfigurations or vulnerabilities can be introduced and exploited at an accelerated pace if proper controls are not in place.
This evolving reality has necessitated a shift from a reactive security posture to a proactive and continuous one. Organizations must embed security into every stage of their cloud journey, from initial design and deployment to ongoing operations and monitoring. This proactive stance ensures that security is an enabler of innovation, not an impediment. The fundamental difference lies in the shared responsibility model, where the cloud provider secures the underlying infrastructure, but the customer is ultimately responsible for securing their data, applications, and configurations within that infrastructure. A clear understanding of this division of labor is the bedrock of effective cloud security. Can any enterprise truly thrive in the digital age without a robust, adaptive cloud security posture that considers every layer of their cloud presence?
Ultimately, robust **cloud security** is not just about protecting against threats; it's about building trust, ensuring business continuity, and unlocking the full potential of cloud innovation safely and responsibly. It is an imperative, not an option.
Architecting Trust: Core Principles and Pillars of Cloud Security
Effective **cloud security** is built upon a foundation of core principles and pillars that guide the design and implementation of protective measures. These principles ensure a holistic and resilient defense, regardless of the cloud service model (IaaS, PaaS, SaaS) or provider. One of the most fundamental principles is the **Shared Responsibility Model**, as briefly introduced. This delineates what the cloud provider secures (the cloud itself: global infrastructure, hardware, software, networking, facilities) and what the customer secures (in the cloud: customer data, applications, operating systems, network configurations, access management). Misunderstanding this shared responsibility is a common and dangerous blind spot.
Beyond this, key security principles derived from traditional information security also apply: **Confidentiality** (protecting data from unauthorized access), **Integrity** (ensuring data is accurate and unaltered), and **Availability** (guaranteeing access to data and systems when needed). These are often referred to as the CIA triad. However, cloud environments introduce specific nuances that require additional emphasis on principles like **Least Privilege**, which dictates that users and services should only have the minimum permissions necessary to perform their tasks. This drastically reduces the potential impact of a compromised account. Complementing this is **Zero Trust**, a modern security model that asserts no user, device, or application should be trusted by default, regardless of whether they are inside or outside the network perimeter. Every access request is authenticated, authorized, and continuously validated.
Other critical pillars include **Data Governance and Compliance**, ensuring that data protection policies align with regulatory requirements (e.g., GDPR, HIPAA, PCI DSS). This involves data classification, retention policies, and robust audit trails. The Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM) provides a comprehensive framework of security controls and best practices, acting as a valuable guide for organizations building their cloud security programs. What fundamental tenets must underpin every cloud security strategy to truly build an unyielding digital fortress against both known and emerging threats?
By diligently adhering to these core principles—from understanding shared responsibility and implementing least privilege to embracing zero trust and prioritizing data governance—organizations can architect a cloud environment that is not only agile and scalable but also inherently trustworthy and resilient against the ever-present dangers of the digital world.
Layers of Defense: Key Components of a Comprehensive Cloud Security Strategy
A truly comprehensive **cloud security** strategy is not a single solution but a carefully orchestrated set of layers, each addressing specific vulnerabilities and working in concert to provide end-to-end protection. Understanding these key components is crucial for designing and implementing an effective defense. Foremost among these is **Identity and Access Management (IAM)**. This component controls who (or what) can access cloud resources and what actions they are permitted to perform. Robust IAM involves multi-factor authentication (MFA), role-based access control (RBAC), and strict user provisioning/deprovisioning processes. Properly configured IAM is the gatekeeper of your cloud environment, preventing unauthorized access and minimizing the blast radius of compromised credentials.
**Network Security** in the cloud focuses on protecting the virtual networks that host your applications and data. This includes virtual private clouds (VPCs), subnets, security groups, network access control lists (NACLs), firewalls, and intrusion detection/prevention systems (IDS/IPS). Secure network segmentation isolates critical assets, while robust traffic filtering prevents malicious activity from reaching your workloads. **Cloud Data Security** is another paramount component, encompassing encryption at rest and in transit, data loss prevention (DLP) tools, data masking, and secure backup and recovery strategies. Protecting sensitive data, wherever it resides in the cloud, is arguably the most critical aspect of any security program.
**Compliance and Governance** ensure that your cloud environment adheres to relevant industry standards, regulatory mandates, and internal policies. This involves continuous auditing, logging, and reporting, often automated through cloud-native tools. **Threat Detection and Response** focuses on identifying and reacting to security incidents swiftly. This includes security information and event management (SIEM) systems, cloud security posture management (CSPM) tools, and cloud workload protection platforms (CWPP) that monitor for anomalies, detect threats, and automate response actions. Finally, **Application Security** ensures that applications deployed in the cloud are built with security in mind, from secure coding practices and API security to vulnerability scanning and web application firewalls (WAFs). With so many moving parts, how do organizations effectively orchestrate a layered defense that protects every single facet of their cloud presence against the unpredictable nature of modern cyber threats?
By implementing and continuously managing these diverse but interconnected components, organizations can establish a resilient **cloud security** framework that protects against a wide array of threats, ensures compliance, and maintains operational integrity in the dynamic cloud ecosystem.
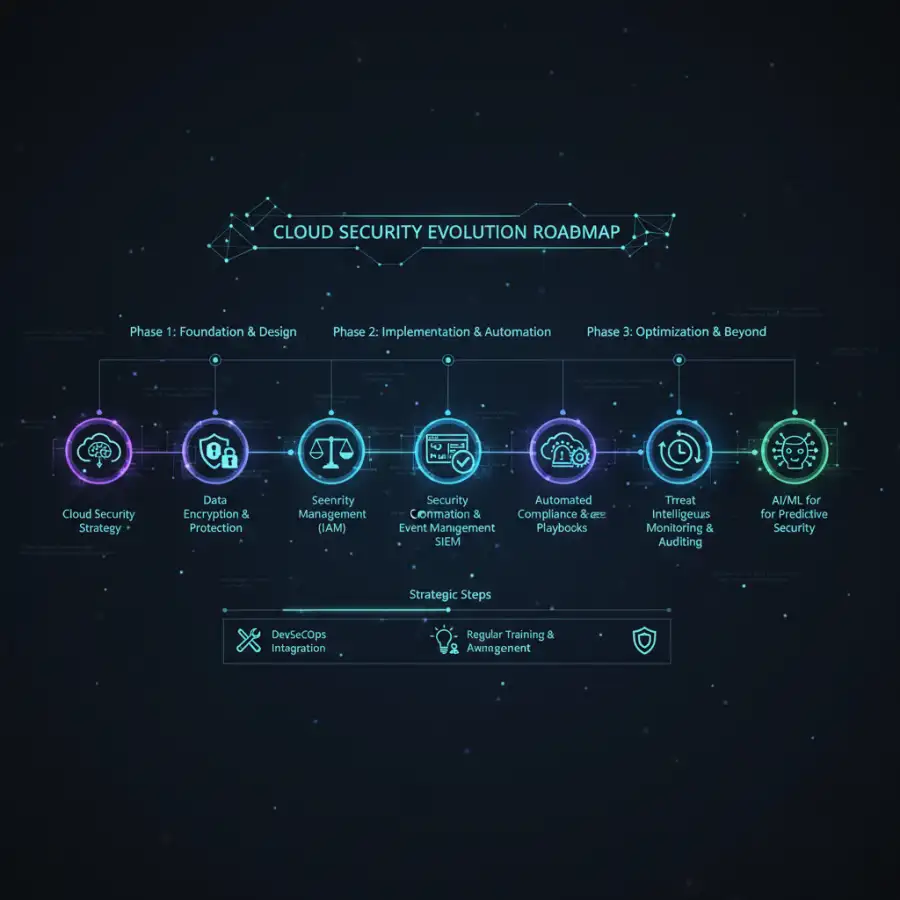
Best Practices in Action: Securing Your Journey Across Google Cloud and AWS
While the core principles of **cloud security** are universal, their implementation often varies significantly across different cloud providers. Understanding and applying best practices specific to platforms like Google Cloud (GCP) and Amazon Web Services (AWS) is crucial for effective defense. Both providers offer a rich suite of native security tools that, when used correctly, can form a formidable protective barrier. For **Identity and Access Management (IAM)**, AWS emphasizes granular control through IAM users, groups, roles, and policies. Best practice dictates using IAM roles for applications and services, implementing least privilege, and enforcing MFA for all users. Google Cloud's IAM is resource-hierarchy based, using organizations, folders, projects, and resources, with policies applied at different levels. Best practices include defining custom roles, using service accounts with minimal permissions, and leveraging Organization Policies to enforce guardrails across your entire GCP environment.
In **Network Security**, AWS offers Virtual Private Clouds (VPCs) with security groups acting as virtual firewalls at the instance level and Network Access Control Lists (NACLs) at the subnet level. Best practices involve segmenting networks, using VPC flow logs for monitoring, and deploying Web Application Firewalls (WAFs) for public-facing applications. Google Cloud's VPC networks similarly provide isolation, with firewall rules allowing fine-grained control over traffic. Leveraging Shared VPC for centralized network management and deploying Cloud Armor for DDoS protection and WAF capabilities are key practices. Are you truly leveraging the native security capabilities built into your chosen cloud provider's platform, or are you inadvertently leaving critical doors ajar for potential adversaries?
For **Cloud Data Security**, both providers offer robust encryption options. AWS Key Management Service (KMS) allows you to create and manage encryption keys, while S3 bucket policies control access to storage. Best practice is to encrypt all data at rest and in transit by default. Google Cloud's Cloud Key Management Service (Cloud KMS) provides similar functionality, and Cloud Storage offers encryption at rest by default. Implementing strong access controls on storage buckets (e.g., preventing public access) is vital for both. For **Threat Detection and Response**, AWS Security Hub aggregates security findings, and Amazon GuardDuty provides intelligent threat detection. Google Cloud's Security Command Center offers a centralized view of your security posture across GCP, with Cloud Logging and Cloud Monitoring providing essential audit trails and real-time alerts.
Finally, for continuous security posture management, tools like AWS Config and Google Cloud Security Health Analytics provide continuous auditing against compliance benchmarks and best practices. By actively utilizing these native tools and adhering to platform-specific best practices, organizations can build highly secure, compliant, and resilient cloud environments tailored to their chosen provider, effectively managing their cloud data security and overall infrastructure.
What this means for you
This deep dive into **cloud security** provides you with a crucial educational foundation, transforming a complex and often intimidating subject into an actionable roadmap for safeguarding your digital assets. What this means for you is the empowerment to confidently navigate the cloud landscape, whether you're a developer, an IT manager, or a business leader. First, you now possess a clear understanding of the **shared responsibility model**. This knowledge is paramount, allowing you to correctly delineate your security obligations from those of your cloud provider, thus preventing dangerous misconceptions that often lead to vulnerabilities. You can now articulate precisely where your security responsibilities begin and end.
Second, by comprehending the core principles like least privilege, zero trust, and the CIA triad, you have a philosophical framework for designing and evaluating any cloud security strategy. This allows you to assess current configurations, identify gaps, and propose more robust solutions, ensuring that security is intrinsically woven into your cloud architecture rather than being an afterthought. You can now approach the evaluation of your cloud environment with a critical, informed perspective. How can you translate the theoretical pillars of cloud security into a tangible, actionable roadmap for protecting your specific digital assets and complex infrastructure?
Third, the practical insights into specific services and best practices across Google Cloud and AWS equip you with the practical tools to implement stronger defenses. You understand the importance of granular IAM, network segmentation, robust cloud data security, and proactive threat detection using native cloud tools. This practical knowledge allows you to engage more effectively with cloud architects and security teams, ensuring that your organization is leveraging the full protective capabilities of its chosen platform. Furthermore, applying this understanding to your organization's financial processes, much like understanding a SaaS accounting service complete guide helps you manage your finances, can streamline security budgeting and compliance.
Finally, this guide emphasizes the continuous nature of cloud security. You are now prepared to embrace a mindset of ongoing vigilance, regular audits, and continuous adaptation to emerging threats. This ensures that your cloud environment remains resilient, compliant, and secure, paving the way for sustained innovation and growth without compromising the integrity of your operations or data. This is your comprehensive educational resource for mastering cloud security.

Risks, trade-offs, and blind spots
While the benefits of **cloud security** are undeniable, navigating its complexities involves inherent risks, crucial trade-offs, and common blind spots that, if overlooked, can severely compromise an organization's digital defenses. One of the most prevalent risks is **misconfiguration**. A single incorrectly configured S3 bucket, an overly permissive IAM policy, or a mismanaged firewall rule can expose vast amounts of sensitive data to the public internet, making it a primary cause of cloud breaches. The trade-off here is between rapid deployment and meticulous configuration; speed often comes at the cost of security if not properly managed.
Another significant blind spot is **shadow IT**. When departments or individuals provision cloud resources without the knowledge or oversight of central IT and security teams, it creates unmanaged vulnerabilities that can bypass established security controls. This decentralization, while fostering agility, can inadvertently expose the organization to significant risk. The balance between empowering innovation and enforcing security governance is a constant trade-off. What unseen vulnerabilities or critical misconceptions might silently undermine even the most meticulously planned cloud security architecture, leaving a gaping hole in your defenses?
**Vendor lock-in** and the **complexity of multi-cloud environments** also present risks. Relying too heavily on a single cloud provider's proprietary security tools can make it difficult and costly to migrate to a different provider if business needs change. Managing security across multiple cloud platforms (AWS, GCP, Azure, etc.) introduces significant complexity, requiring specialized tools, processes, and expertise to ensure consistent security policies and visibility. This can lead to increased operational overhead and potential security gaps.
A persistent risk is **skill gaps**. The rapid evolution of cloud technologies means there's a constant shortage of skilled cloud security professionals. Organizations may struggle to find and retain the talent needed to design, implement, and manage complex cloud security architectures. This can lead to reliance on external consultants or, worse, poorly secured environments. Furthermore, balancing **security with agility** is a continuous trade-off. Overly restrictive security policies can hinder development and innovation, while insufficient controls create unacceptable risk. Achieving the right balance requires a continuous cost-benefit analysis of security investments, similar to what you'd find in evaluating the cost-benefit of security investments in other domains. Additionally, understanding your financial infrastructure, potentially through mastering cloud-based financial management, can help align security spending with business objectives. Addressing these risks and understanding these trade-offs is crucial for building a resilient and adaptable **cloud security** strategy.
Main points
- Cloud security is essential for protecting cloud-based data, applications, and infrastructure from evolving cyber threats.
- The Shared Responsibility Model clearly defines security obligations between cloud providers and customers; understanding this is crucial.
- Core principles include Confidentiality, Integrity, Availability (CIA triad), Least Privilege, and Zero Trust.
- Key components of a comprehensive strategy include IAM, Network Security, Cloud Data Security, Compliance, and Threat Detection/Response.
- Leveraging native cloud security tools (e.g., AWS IAM, GCP Security Command Center, KMS) and platform-specific best practices is vital.
- Common risks include misconfigurations, shadow IT, complexity of multi-cloud environments, and skill gaps.
- Balancing security with agility and conducting continuous risk assessment are crucial trade-offs.
- Cloud security is an ongoing journey requiring continuous monitoring, adaptation, and a proactive posture.
Armed with this comprehensive understanding, you are now better prepared to navigate the complexities of cloud security. Take the next step to audit your current posture, implement best practices, and fortify your digital frontier for unwavering protection.

