The Future of Endpoint Security: Decoding EDR, XDR, and MDR for Robust Cyber Defense
Navigating the Evolving Landscape of Threat Detection, Response, and Managed Services
Are you grappling with the alphabet soup of modern cybersecurity solutions, wondering if EDR, XDR, or MDR is truly the answer to your organization's evolving threats? Demystify the landscape and discover your optimal defense strategy.
Imagine a security posture so resilient it anticipates attacks, rapidly contains breaches, and frees your team to innovate, rather than constantly react. Uncover the distinctions that lead to truly proactive protection.
From subtle endpoint anomalies to widespread network intrusions, today's cyber threats are relentless. This guide provides the clarity you need to choose the right tools and services, securing your digital future against an ever-changing adversary.
In the relentlessly evolving landscape of cyber threats, traditional perimeter defenses are no longer sufficient. Attackers are increasingly sophisticated, targeting every possible entry point, with endpoints—laptops, desktops, servers, mobile devices—remaining primary vectors for initial compromise. This reality has driven the evolution of endpoint security beyond conventional antivirus, leading to a new generation of acronyms: EDR, XDR, and MDR. For many security leaders and IT professionals, understanding the definitions, core differences, unique features, advantages, disadvantages, and optimal use cases for these solutions has become a critical challenge. The stakes are high; choosing the right strategy determines an organization's ability to detect, respond to, and ultimately prevent devastating cyberattacks. The "future of endpoint security EDR" is not a singular path but a diverse, interconnected ecosystem where these technologies integrate, overlap, and continually evolve.
This comprehensive guide aims to thoroughly demystify EDR (Endpoint Detection and Response), XDR (Extended Detection and Response), and MDR (Managed Detection and Response), alongside related foundational technologies like EPP (Endpoint Protection Platform), SIEM (Security Information and Event Management), and NDR (Network Detection and Response). We will explore how these solutions function independently, how they integrate to form a more holistic defense, and crucially, how they are shaping the overall cybersecurity strategy for organizations of all sizes. By the end of this comprehensive comparison, you will be equipped to choose the best cybersecurity strategy to safeguard your digital assets effectively.
Quick navigation
- Foundations of Cybersecurity: EPP, SIEM, and NDR
- EDR: The Evolution of Endpoint-Focused Defense
- XDR: Expanding the Horizon of Detection and Response
- MDR: Security Expertise as a Service
- What this means for you
- The Interplay: Integration, Overlap, and Differentiation
- Risks, trade-offs, and blind spots
- Strategic Selection: Choosing the Right Solution for Your Organization
- Main points
Foundations of Cybersecurity: EPP, SIEM, and NDR
Before diving into the intricacies of EDR, XDR, and MDR, it’s essential to understand the foundational technologies that paved the way for their emergence. Cybersecurity has always been a race against time and ingenuity, but what exactly necessitated this rapid evolution in threat detection and response?

Endpoint Protection Platform (EPP)
Historically, endpoint protection began with antivirus (AV) software, designed to detect and block known malware signatures. The modern Endpoint Protection Platform (EPP) evolved from this, offering a broader suite of capabilities, including antivirus, anti-malware, firewall, intrusion prevention, and web filtering. EPP primarily focuses on *preventing* threats from executing on an endpoint using signature-based detection, heuristics, and some behavioral analysis. It's a critical first line of defense, but it often struggles with sophisticated, unknown, or file-less attacks that bypass traditional prevention methods.
Security Information and Event Management (SIEM)
SIEM platforms are designed to collect, aggregate, and analyze security logs and event data from various sources across an entire IT infrastructure—endpoints, networks, servers, applications, cloud environments. Their goal is to provide a centralized view of security events, detect anomalies, and generate alerts. While powerful for correlation and compliance, SIEMs can be complex, costly to implement and manage, and often require significant in-house expertise to tune rules and effectively triage the high volume of alerts they generate.
Network Detection and Response (NDR)
NDR solutions focus on monitoring network traffic in real-time to detect suspicious activities, anomalies, and potential threats that might bypass endpoint or perimeter defenses. They provide visibility into north-south (client-server) and east-west (server-to-server) traffic, using behavioral analytics and machine learning to identify lateral movement, command-and-control communication, and data exfiltration. NDR complements EPP and SIEM by offering another critical layer of detection, specifically at the network level.
EDR: The Evolution of Endpoint-Focused Defense
Endpoint Detection and Response (EDR) marked a significant leap beyond traditional EPPs. It recognized that prevention alone was insufficient and that sophisticated threats would inevitably breach initial defenses. How did EDR fundamentally shift the paradigm from simply blocking known threats to actively hunting and responding to them?
What is EDR?
EDR systems continuously monitor and record all activity on endpoints—processes, file changes, network connections, user behavior—to detect and investigate suspicious activities. Unlike EPP, which primarily prevents, EDR focuses on the *detection, investigation, and response* to advanced threats that have bypassed initial defenses. It provides deep visibility into what's happening on an endpoint, allowing security teams to understand the full scope of an attack.
Core Features of EDR:
- Continuous Monitoring and Data Collection: Gathers rich telemetry data from endpoints.
- Threat Detection: Uses behavioral analytics, machine learning, and threat intelligence to identify suspicious patterns and indicators of compromise (IoCs).
- Threat Hunting: Enables security analysts to proactively search for hidden threats and attack patterns using collected data.
- Investigation Capabilities: Provides detailed context for alerts, allowing analysts to trace attack paths, identify affected systems, and understand the root cause.
- Response Actions: Offers capabilities to isolate compromised endpoints, terminate malicious processes, remove persistence mechanisms, and roll back changes.
Advantages of EDR:
- Enhanced Visibility: Provides granular insight into endpoint activity, crucial for understanding and responding to attacks.
- Improved Detection of Advanced Threats: Excels at identifying file-less attacks, zero-days, and polymorphic malware that EPPs miss.
- Faster Incident Response: Equips security teams with the tools to quickly investigate and contain breaches, reducing dwell time.
- Proactive Threat Hunting: Shifts security from reactive to proactive, allowing teams to find threats before they cause significant damage.
Disadvantages of EDR:
- Requires Skilled Analysts: EDR tools are powerful but demand experienced security personnel to operate, interpret alerts, and conduct threat hunting.
- Alert Fatigue: Can generate a high volume of alerts, necessitating careful tuning and prioritization to avoid overwhelming security teams.
- Endpoint-Centric: While deep, EDR's visibility is limited to the endpoint itself, potentially missing threats originating or spreading solely on the network or in other domains.
XDR: Expanding the Horizon of Detection and Response
Recognizing EDR's endpoint-centric limitations, Extended Detection and Response (XDR) emerged as the next evolutionary step. It aims to unify and correlate security data from a broader range of sources beyond just endpoints. If EDR provides a microscope on the endpoint, how does XDR expand this view to offer a panoramic security perspective?
What is XDR?
XDR is a unified security incident detection and response platform that automatically collects and correlates security data from *multiple* security layers—endpoints, networks, cloud environments, identity, and applications. Its primary goal is to provide a holistic view of threats, offering richer context and automated remediation capabilities across the entire digital estate, reducing alert noise and improving detection accuracy compared to siloed tools or traditional SIEMs.
Core Features of XDR:
- Centralized Data Ingestion: Gathers telemetry from EDR, NDR, cloud security, email security, identity management, etc.
- Cross-Domain Correlation: Uses AI and machine learning to correlate events across these diverse data sources, linking seemingly disparate activities into comprehensive attack narratives.
- Advanced Analytics: Uses sophisticated analytics to identify complex attack patterns, insider threats, and subtle anomalies that span multiple domains.
- Automated & Orchestrated Response: Can automatically initiate response actions across different security tools (e.g., isolate an endpoint, block an IP at the firewall, disable a user account).
- Simplified Workflows: Streamlines security operations by consolidating alerts and providing a unified console for investigation and response.
Advantages of XDR:
- Holistic Threat Visibility: Provides a much broader and deeper understanding of an attack's scope, including lateral movement and multi-stage campaigns.
- Reduced Alert Fatigue: Correlates low-fidelity alerts into high-fidelity incidents, significantly cutting down on noise and false positives.
- Faster and More Effective Response: Enables automated and orchestrated responses across the security stack, leading to quicker containment and remediation.
- Improved Security Operations Efficiency: Consolidates tools and simplifies workflows, making security teams more productive.
Disadvantages of XDR:
- Vendor Lock-in: Many XDR solutions are proprietary, relying on data from a single vendor's security products, which can limit integration with existing third-party tools.
- Implementation Complexity: While simpler than a full-blown SIEM, implementing XDR still requires careful planning and integration, especially in complex environments.
- Evolving Definition: The XDR market is still maturing, and definitions and capabilities can vary significantly between vendors.
MDR: Security Expertise as a Service
While EDR and XDR provide powerful tools, they still require skilled human analysts to operate them effectively. This is where Managed Detection and Response (MDR) services step in, offering a solution for organizations that lack the in-house cybersecurity expertise or resources. How does MDR address the critical talent gap, transforming raw security data into actionable, expert-driven protection?
What is MDR?
MDR is an outsourced security service that provides customers with 24/7 threat monitoring, detection, and response capabilities. It combines advanced technology (often EDR or XDR platforms) with human expertise (security analysts, threat hunters, incident responders) to proactively protect organizations. Instead of simply providing a tool, MDR offers security as a service, actively managing the detection and response lifecycle on your behalf.
Core Features of MDR:
- 24/7 Monitoring and Alert Triage: Continuous surveillance of your security environment by expert analysts.
- Proactive Threat Hunting: Human threat hunters actively search for hidden threats, not just reacting to alerts.
- Expert Incident Response: When a threat is detected, the MDR provider takes swift action to investigate, contain, and often remediate the incident.
- Vulnerability Management: May include recommendations for strengthening security posture and addressing vulnerabilities.
- Reporting and Guidance: Provides regular reports on security posture, detected threats, and actionable recommendations.
Advantages of MDR:
- Access to Expert Security Personnel: Fills the cybersecurity talent gap by providing immediate access to skilled analysts and threat hunters.
- 24/7 Coverage: Ensures continuous protection, even outside of business hours, which is critical for global organizations or those with limited staff.
- Faster and More Effective Response: Expert teams can respond to incidents much quicker than overstretched in-house teams.
- Reduced Operational Burden: Offloads the day-to-day management of security tools, allowing internal IT teams to focus on core business operations.
- Predictable Costs: Often provided on a subscription basis, offering clear and predictable cybersecurity expenditure.
Disadvantages of MDR:
- Loss of Direct Control: You're outsourcing critical security functions, meaning less direct control over the day-to-day security operations.
- Integration Challenges: Requires robust integration with your existing IT infrastructure to be fully effective.
- Cost: Can be more expensive than simply licensing EDR or XDR software, but the cost often justifies the value of expert management.
What this means for you
Navigating the intricate world of EDR, XDR, and MDR is more than an academic exercise; it's a critical strategic imperative for safeguarding your organization's future. The distinctions between these advanced security solutions directly impact your ability to detect, respond to, and ultimately prevent the most sophisticated cyber threats. How does truly understanding this evolving landscape translate into a more resilient, efficient, and future-proof cybersecurity posture for your business?
Firstly, this comprehensive comparison helps you move beyond marketing hype and make truly informed decisions about your cybersecurity investments. You can now critically assess vendor claims, identify solutions that genuinely address your specific threat landscape and operational capabilities, and confidently allocate resources to technologies that deliver tangible protection and value. This clarity minimizes wasted spending on overlapping or inadequate tools, ensuring every security dollar is spent wisely, helping you achieve a better ROI revolution cost-benefit from your security investments.
Secondly, by understanding the nuanced integration and overlap of these solutions, you can build a more cohesive and robust security ecosystem. Whether you choose to build a security operations center (SOC) with EDR and SIEM, streamline with XDR, or utilize the expert services of MDR, you now possess the knowledge to design a layered defense that provides comprehensive visibility and rapid response across all critical domains. This integrated approach reduces blind spots and enhances your organization's overall threat posture.
Ultimately, this deep dive into the future of endpoint security EDR and its counterparts means moving from reactive firefighting to proactive threat management. You can better anticipate emerging risks, fine-tune your defenses, and ensure that your security strategy evolves as rapidly as the threats themselves. This strategic advantage not only protects your assets and reputation but also fosters a more secure environment where innovation can flourish without constant fear of cyber disruption. Your organization gains the confidence to operate securely, knowing its defenses are built on a solid foundation of understanding and strategic choice.
The Interplay: Integration, Overlap, and Differentiation
These advanced security solutions don't exist in a vacuum; they integrate with and sometimes overlap with other critical components of an organization's security architecture. Understanding these relationships is key to building a truly resilient defense. How do EDR, XDR, and MDR interact with the broader security ecosystem, and where do their functionalities converge or diverge?
EDR and EPP: A Cohesive Endpoint Defense
EDR and EPP are not mutually exclusive; in fact, they are often integrated into a single endpoint security platform. EPP handles the preventative heavy lifting (blocking known threats), while EDR provides the detection and response capabilities for advanced attacks that bypass EPP. Modern endpoint security solutions typically combine both functionalities, offering a layered approach to endpoint protection.
XDR's Evolution from EDR and SIEM
XDR can be seen as an evolution, or perhaps a more focused alternative, to traditional SIEM and an extension of EDR. Where SIEM aggregates *all* logs (including non-security data) and requires extensive tuning, XDR focuses specifically on security data from a curated set of sources, making it potentially easier to implement and manage. Many XDR solutions utilize and build upon the EDR agent for their endpoint telemetry. While a SIEM might offer comprehensive data aggregation, XDR focuses on the security-specific aspects that provide immediate threat context. This is particularly relevant when considering the vast amount of data generated by modern tools, similar to how organizations approach mastering Sage Intacct SaaS ultimate, where efficient data management is key.
MDR's Utilization of EDR/XDR Technology
MDR is a *service* layer built on top of underlying technology. Many MDR providers deploy their own or third-party EDR or XDR platforms within their clients' environments. The MDR service then actively monitors, manages, and responds to threats detected by these platforms, essentially providing the human expertise needed to extract maximum value from the technology. This means that an organization might license an EDR or XDR solution, but then also subscribe to an MDR service to manage it.
NDR and XDR: Complementary Visibility
NDR focuses on network traffic, providing visibility into threats moving across the network. XDR, with its cross-domain correlation, can ingest data from NDR solutions to gain an even richer understanding of an attack. If EDR sees what's happening *on* a device and NDR sees what's happening *between* devices, XDR stitches these views together for a more complete picture, particularly crucial in today's cloud-heavy environments where network boundaries are blurred.
The Move Towards Consolidation and Automation
The overarching trend is toward consolidation and automation. Organizations are seeking fewer, more integrated tools that provide broader visibility and can orchestrate responses automatically. This reduces the complexity of managing disparate security products and frees up security teams to focus on strategic initiatives rather than manual correlation and alert triage.
Risks, trade-offs, and blind spots
While EDR, XDR, and MDR offer advanced capabilities, no solution is a silver bullet. Organizations must be acutely aware of the inherent risks, strategic trade-offs, and potential blind spots when implementing these technologies and services. What seemingly advantageous choice could introduce unforeseen vulnerabilities or operational challenges down the line?
Vendor Lock-in and Integration Challenges
One significant risk, particularly with some XDR solutions, is vendor lock-in. Many XDR platforms are designed to work optimally, or exclusively, with their vendor's proprietary security stack. This can limit an organization's flexibility to choose best-of-breed components from other vendors, potentially leading to suboptimal integrations or forcing a complete overhaul of existing security infrastructure. The trade-off is often between the simplicity of a single-vendor XDR solution and the desire for a more open, customizable security ecosystem.
The Skill Gap for EDR/XDR Management
While EDR and XDR provide powerful tools, they are not set-and-forget solutions. They require skilled security analysts to manage, tune, interpret alerts, and perform proactive threat hunting. A common blind spot is underestimating the human capital investment required to effectively operate these platforms. Without sufficient in-house expertise, organizations risk alert fatigue, missed threats, and underutilization of their expensive technology. The trade-off is investing in training and recruiting highly specialized personnel versus outsourcing to an MDR provider.
Scope Limitations and Uncovered Attack Surfaces
Despite their advanced capabilities, each solution has its inherent scope. EDR is endpoint-centric. While XDR extends this, its coverage is dependent on the data sources it ingests. A blind spot can be assuming that implementing one of these solutions automatically covers *all* potential attack surfaces. For example, specific legacy systems, IoT devices, or highly specialized operational technology (OT) environments might require dedicated security solutions not fully addressed by EDR/XDR/MDR. The trade-off is between a broadly effective solution and the need for niche, specialized security for specific assets.
Over-reliance on Automation and AI
While automation and AI are critical components of XDR and MDR, an over-reliance on them can be a risk. Sophisticated attackers continuously evolve their tactics, techniques, and procedures (TTPs) to evade automated defenses. A blind spot is believing that technology alone can solve all security problems. Human threat hunters and incident responders provide invaluable contextual analysis, intuition, and creative problem-solving that AI currently cannot replicate. The trade-off is balancing automated efficiency with the indispensable critical thinking of human analysts.
The "MDR Black Box" Phenomenon
With MDR, you outsource a significant portion of your security operations. A potential blind spot here is the "black box" phenomenon, where organizations have limited visibility into the day-to-day operations of their MDR provider. This can lead to a lack of understanding of what threats are being seen, how they are being responded to, or even a dependency on the provider for critical security insights. The trade-off is the convenience of outsourcing versus maintaining a degree of transparency and control over your security posture. Always ensure your MDR contract includes clear reporting, communication protocols, and access to raw data or dashboards, similar to ensuring transparency with any outsourced SaaS accounting service complete guide provides.
Strategic Selection: Choosing the Right Solution for Your Organization
Selecting the right cybersecurity strategy from among EDR, XDR, and MDR is not a one-size-fits-all decision. It requires a careful assessment of your organization's unique needs, resources, and risk tolerance. With such diverse capabilities and operational models, how does an organization intelligently determine which solution best aligns with its current security maturity and future aspirations?
When to Choose EDR:
- Maturity Level: Organizations with a foundational security program already utilizing EPP, but seeking deeper visibility, threat hunting capabilities, and faster response specifically at the endpoint level.
- Resources: Have a dedicated, skilled security operations team capable of managing EDR alerts, conducting investigations, and executing response actions.
- Budget: Looking for a cost-effective step up from traditional endpoint protection without the broader scope or higher cost of XDR or MDR.
- Focus: Primary concern is enhancing endpoint detection and response, with other security domains managed by separate, mature tools.
When to Choose XDR:
- Maturity Level: Organizations with multiple security tools and data silos, struggling with alert fatigue, and seeking to consolidate, correlate, and automate detection and response across diverse domains (endpoint, network, cloud, identity).
- Resources: Possess a capable security team but aim to improve their efficiency and effectiveness by providing a unified view and streamlined workflows. They want to *enhance* their SOC, not necessarily replace it with a service.
- Budget: Willing to invest in a more comprehensive platform that offers greater visibility and automation than EDR, potentially reducing overall tool sprawl and operational costs in the long run.
- Focus: Desire a holistic view of the attack surface, improved threat context, and orchestrated response capabilities across their digital environment.
When to Choose MDR:
- Maturity Level: Organizations of any size that lack sufficient in-house cybersecurity expertise, staff, or 24/7 coverage. This includes small to medium businesses (SMBs) or larger enterprises with lean security teams.
- Resources: Limited staff or budget for building and maintaining a full-fledged Security Operations Center (SOC). They need outsourced expertise for continuous monitoring, threat hunting, and incident response.
- Budget: Prioritize predictable costs and guaranteed security outcomes over building an in-house team.
- Focus: Need active, expert-driven protection and response, freeing their internal IT teams to focus on core business functions.
The Hybrid Approach:
It's also common for organizations to adopt a hybrid approach. For example, an organization might implement EDR in-house and then use an MDR service specifically for 24/7 monitoring and response, utilizing their internal team for more strategic threat hunting or higher-level security architecture. The choice often evolves with an organization's growth and changing threat landscape.
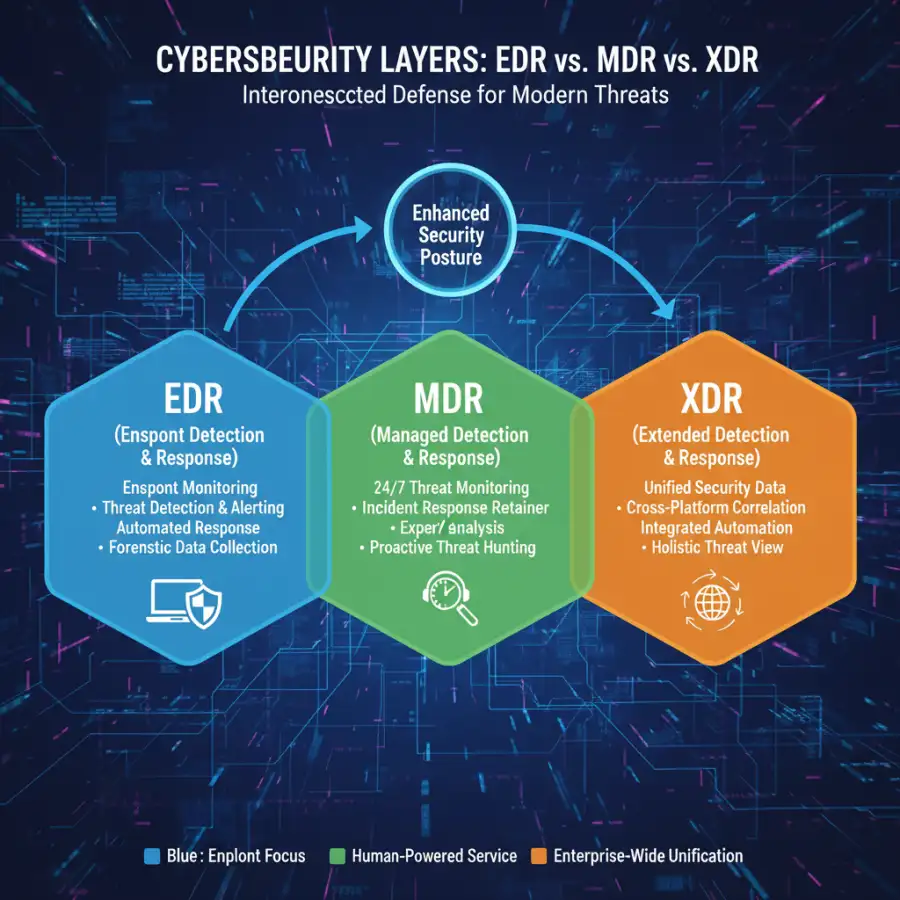
Main points
Navigating the complex world of modern cybersecurity requires a clear understanding of EDR, XDR, and MDR to build a robust defense. Here are the core takeaways:
- EDR is Endpoint-Focused: Continuously monitors and records endpoint activity for deep threat detection, investigation, and response.
- XDR Offers Extended Visibility: Unifies security data from multiple domains (endpoints, network, cloud, identity) for holistic threat correlation and automated response.
- MDR Provides Expert Service: An outsourced service combining technology (often EDR/XDR) with human experts for 24/7 monitoring, hunting, and incident response.
- EPP, SIEM, NDR Provide Context: These foundational technologies complement or are integrated within EDR/XDR/MDR solutions.
- Choose Based on Need and Resources: Match the solution to your organization's security maturity, in-house expertise, budget, and desired scope of coverage.
- Beware of Risks and Trade-offs: Consider vendor lock-in, the need for skilled analysts, scope limitations, and potential over-reliance on automation.
- Integration is Key: Maximize effectiveness by ensuring proper integration with your existing security stack for a cohesive defense.
- The Future is Unified and Managed: Trends point towards consolidated, automated platforms and/or outsourced expertise to combat evolving cyber threats.
Equipped with this knowledge, confidently assess your organization's cybersecurity needs. Evaluate your current threat landscape and internal resources to choose the optimal EDR, XDR, or MDR strategy that secures your digital future.

