Understanding Digital Access: A Guide to IAM, PAM, PIM, and IGA
Clarifying the fundamental principles of identity and access management for building secure digital environments and making informed career choices.
Do you truly understand the intricate layers of digital access control, or are the acronyms IAM, PAM, PIM, and IGA blurring into a confusing cybersecurity alphabet soup?
Imagine a world where every user, every privilege, and every identity is precisely managed, preventing breaches and securing your most critical digital assets.
Discover how to build a robust cloud security architecture, turning potential weaknesses into strong defenses that protect your digital future.
In today’s hyper-connected enterprise, managing who can access what, when, and how, has become one of the most critical challenges for cybersecurity professionals. The sheer volume of digital identities—from human users and external partners to machines and API endpoints—and the proliferation of systems they need to interact with, create an intricate web of access points. Navigating this complexity requires more than just basic passwords; it demands a strategic, layered approach.
This is where frameworks like Identity and Access Management (IAM), Privileged Access Management (PAM), Identity Governance and Administration (IGA), and even the nuanced concept of Privilege Identity Management (PIM) come into play. While these terms often appear in cybersecurity discussions, their precise definitions, distinctions, and symbiotic relationships can be a source of considerable confusion. This guide clarifies these vital concepts, comparing IAM, PAM, and PIM, and explaining the role of IGA. By understanding how these frameworks fit together, you can build more robust digital defenses, meet compliance obligations, and make informed decisions that strengthen your organization's security posture and potentially your career in this essential field.
Quick navigation
- The Foundation: What is Identity and Access Management (IAM)?
- Elevated Control: What is Privileged Access Management (PAM)?
- Identity Governance and Administration (IGA) and Privilege Identity Management (PIM): The Orchestrators
- What this means for you
- The Symbiotic Relationship: How They Work Together
- Risks, trade-offs, and blind spots
- Main points
The Foundation: What is Identity and Access Management (IAM)?
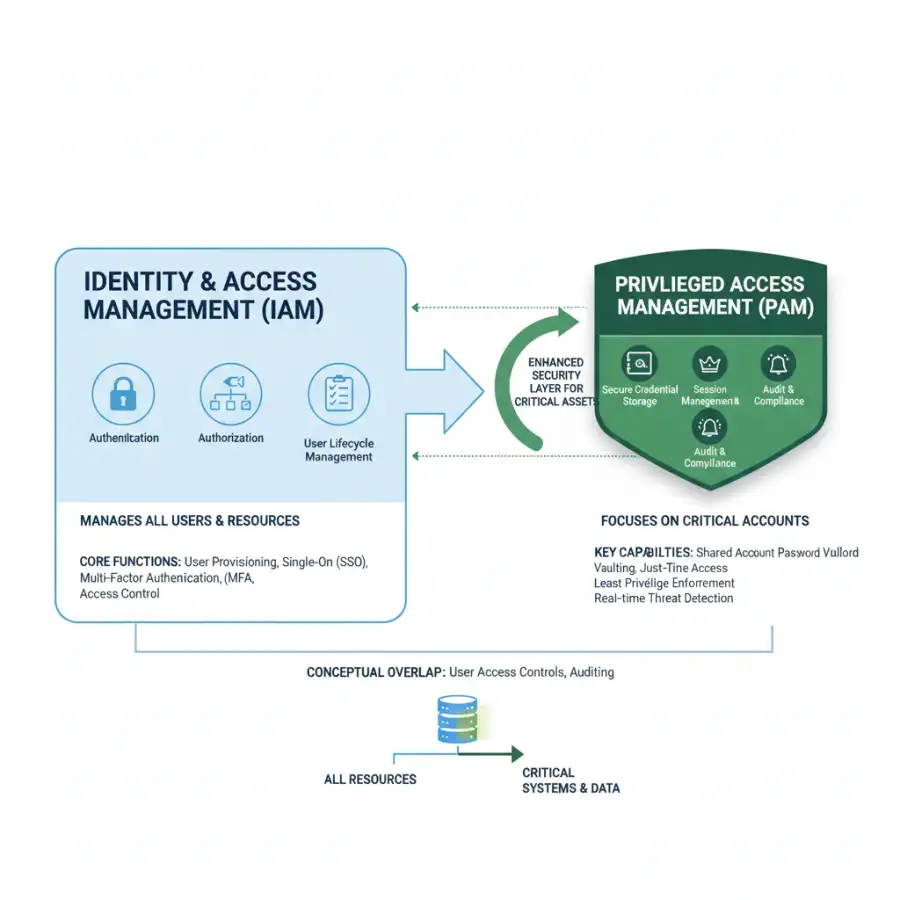
Identity and Access Management (IAM) serves as the bedrock of any modern security strategy. It is the comprehensive framework that dictates how users are identified and how their access to various digital resources is controlled. Think of it as the ultimate gatekeeper for your digital ecosystem, ensuring that only the right people (or machines) can access the right resources at the right time. IAM isn't just a technology; it's a set of business processes, policies, and supporting technologies.
The core functions of IAM are straightforward yet powerful. Firstly, there's authentication, which verifies a user's identity—proving who they claim to be through methods like passwords, biometrics, or security tokens. Secondly, authorization determines what an authenticated user is permitted to do once inside a system or application. This involves assigning specific roles and permissions. Beyond these, IAM encompasses crucial aspects like user lifecycle management, which includes the provisioning (creating access), deprovisioning (removing access), and modification of user accounts as individuals join, move within, or leave an organization. This ensures that access rights are always current and revoked promptly when no longer needed.
Other vital components of a robust IAM system include Single Sign-On (SSO), which allows users to log in once and gain access to multiple interconnected systems without re-entering credentials, significantly improving user experience and reducing password fatigue. Multi-Factor Authentication (MFA) adds an extra layer of security by requiring users to provide two or more verification factors to gain access, drastically reducing the risk of unauthorized access even if a password is compromised. Critically, IAM is not limited to human users; it manages the identities and access of *all* entities, including applications, services, APIs, and IoT devices. It's about securing every digital interaction point. How can an organization effectively secure its perimeter if it can't even confidently identify who is knocking at the door?
Ultimately, a strong IAM strategy aims to minimize the attack surface by ensuring that access is always controlled, logged, and audited, providing visibility into who is accessing what, and when. It forms the essential first line of defense in protecting sensitive data and systems from both internal and external threats.
Elevated Control: What is Privileged Access Management (PAM)?
While IAM focuses on managing access for all identities, Privileged Access Management (PAM) narrows that focus to a highly critical subset: privileged accounts. These are the "keys to the kingdom" – accounts with elevated permissions that can access sensitive data, configure critical systems, install software, or make significant changes to the IT infrastructure. Examples include administrator accounts, root accounts, service accounts, and emergency break-glass accounts. The compromise of a single privileged account can lead to catastrophic data breaches, system downtime, and regulatory non-compliance.
PAM is therefore a specialized, hyper-focused subset of IAM, designed to secure, monitor, and manage these high-risk accounts. It recognizes that not all identities are created equal, and those with elevated powers require a far more stringent set of controls. The core objective of PAM is to prevent unauthorized access to privileged accounts, protect against misuse of legitimate privileged access, and establish a clear audit trail of all privileged activities. Imagine guarding the crown jewels; you wouldn't use the same security measures for general entry as you would for the vault itself.
Key features of PAM solutions include privileged session management, which records and monitors all activities during a privileged session, allowing for real-time threat detection and forensic analysis. Password vaulting securely stores and rotates privileged credentials, removing the need for humans to know or manage these sensitive passwords directly. Just-in-Time (JIT) access grants privileged access only when needed, for a limited time, and for a specific task, eliminating standing privileges that could be exploited. This dynamic approach significantly reduces the window of opportunity for attackers. Furthermore, PAM systems provide detailed audit trails of all privileged actions, crucial for compliance and post-incident investigation. They often incorporate threat detection for privileged sessions, using behavioral analytics to flag unusual activity that might indicate an attack or insider threat. If an attacker gains control of your most powerful accounts, what good are your perimeter defenses?
By implementing a robust PAM strategy, organizations can dramatically reduce the risk associated with privileged credentials, enforcing the principle of least privilege at the highest level and ensuring accountability for all high-impact actions within their digital infrastructure.
Identity Governance and Administration (IGA) and Privilege Identity Management (PIM): The Orchestrators
As organizations grow, the complexity of managing identities and access across numerous systems, applications, and cloud services can become overwhelming. This is where Identity Governance and Administration (IGA) steps in. IGA is a holistic framework that automates and streamlines the management of digital identities and their associated access rights, with a strong emphasis on compliance, audit, and risk reduction. It acts as an orchestrator, ensuring that access policies are enforced consistently across the entire IT landscape.
The primary functions of IGA include access request and approval workflows, automating the process of granting or revoking access based on predefined policies. It also facilitates regular access reviews and certification campaigns, where managers or resource owners periodically verify that users still require their current access privileges, helping to prevent privilege creep. Role management is another key aspect, defining standardized roles with specific sets of permissions, making access provisioning more efficient and less prone to error. Crucially, IGA also enforces Segregation of Duties (SoD), preventing users from having conflicting access rights that could lead to fraud or error, such as a single person being able to both approve and process payments. Can any organization truly understand its attack surface without a clear, auditable picture of every identity and its entitlements?

Now, let's address Privilege Identity Management (PIM). This term is often used interchangeably with PAM, which can lead to confusion. However, in some contexts, PIM is seen as a broader, more strategic approach within IGA that focuses on the *governance* and *lifecycle* of all privileged identities, including human and non-human privileged accounts. While PAM often refers to the specific technologies and tools used to *control* privileged access (e.g., password vaults, session monitoring), PIM encompasses the policies, processes, and strategic oversight for how these privileged identities are defined, managed, and audited across the organization. It's about ensuring the *right* privileged identity is granted, while PAM is about securing the *access* itself. For organizations managing complex systems or ensuring accountability, understanding the robust processes that govern privileged identities is as critical as mastering specific platforms, much like the detailed understanding required for mastering Sage Intacct SaaS for comprehensive financial management.
IGA and PIM (in its broader sense) ensure that all access, especially privileged access, is consistent with business policy and regulatory requirements. They provide the necessary visibility and automation to manage the identity lifecycle at scale, transforming what would otherwise be a chaotic and error-prone manual process into a structured, auditable, and secure operation. This level of governance is indispensable for organizations aiming for high levels of security and compliance.
What this means for you
The strategic implementation of IAM, PAM, PIM, and IGA isn't just about adhering to cybersecurity best practices; it translates into tangible benefits for both businesses and individual professionals. These frameworks collectively offer a robust defense against an increasingly sophisticated threat landscape, while also streamlining operations and fostering career growth.
For Businesses, the impact is profound. Firstly, there's a significant reduced risk of insider threats and external breaches. By meticulously managing identities and access, especially privileged ones, organizations can prevent unauthorized access, detect suspicious activity, and mitigate the damage from compromised credentials. This direct reduction in risk protects sensitive data, intellectual property, and critical infrastructure. Secondly, these solutions drive improved compliance with a myriad of regulations (GDPR, HIPAA, PCI DSS, SOX). IGA, in particular, provides the auditable trails and automated access reviews necessary to demonstrate adherence to these strict mandates, helping businesses avoid costly fines and reputational damage. The justification for such security investments often lies in a compelling ROI analysis, demonstrating the long-term value against potential breach costs.
Furthermore, businesses experience heightened operational efficiency. Streamlined user provisioning and deprovisioning, automated access requests, and SSO capabilities mean less administrative overhead for IT teams. Employees gain faster, more seamless access to the resources they need, boosting productivity. The enhanced auditability provided by these systems also simplifies internal and external audits, saving considerable time and resources. For example, a global corporation can quickly identify and revoke access for a departing employee across hundreds of applications, or a financial institution can demonstrate a pristine audit trail of all privileged database access during a regulatory review. How much is a single data breach truly costing your organization, not just in dollars, but in trust and future potential?
For Individuals aspiring to or working in cybersecurity, understanding these concepts is absolutely crucial. They represent high-demand skills that are foundational for roles such as cybersecurity architects, analysts, and engineers. Proficiency in designing, implementing, and managing IAM, PAM, and IGA solutions makes you an invaluable asset in the job market. This knowledge is also essential for interview readiness, as these topics are frequently explored in technical and strategic cybersecurity roles. A deep grasp of how these systems fit together and their practical implications will set you apart, enabling you to make informed decisions about cybersecurity strategies and career paths alike.
The Symbiotic Relationship: How They Work Together
It's crucial to understand that IAM, PAM, PIM, and IGA are not isolated, competing tools but rather interlocking layers that form a comprehensive, holistic security strategy. Each plays a distinct yet complementary role, much like different sections of a secure building. Dismissing one for another would be akin to having a strong front door but leaving the back windows open.
At the broadest level, IAM is the foundational layer. It establishes and manages the identities of all users (human and non-human) and determines their baseline access to various resources across the organization. It ensures that every user is who they say they are and can access what they generally need for their day-to-day tasks. Think of IAM as setting up all the standard user accounts and their basic office access cards.
Layered on top of IAM, PAM steps in to secure the critical "keys to the kingdom." It takes those identities that have elevated privileges (the "master keys") and subjects them to much stricter controls. PAM ensures that these highly powerful accounts are vaulted, monitored, and accessed only when absolutely necessary, often with just-in-time provisioning. If IAM gives you an office access card, PAM guards the single, special key that unlocks the server room, and makes sure you only use it when you actually need to go in, for a documented reason.
PIM (Privilege Identity Management), in its strategic sense, works alongside PAM by providing the overarching policy and governance for *all* privileged identities. It defines *who* can be a privileged user, *how* those privileges are requested and approved, and *when* they are revoked. It’s the policy document that dictates how the server room key is requested, approved, and returned. While PAM is the technological control, PIM provides the strategic framework for that control. Finally, IGA acts as the orchestrator and auditor across all these layers. It automates the lifecycle of identities and access rights, ensuring that the policies defined by PIM are enforced, that IAM provisioning is accurate, and that all access, especially privileged access, is regularly reviewed and certified for compliance. IGA is the security manager who ensures all policies are followed, conducts regular audits of all key usage, and automatically updates access based on job changes.
Together, this symbiotic relationship creates a powerful defense: IAM establishes all identities, PAM tightly secures the most critical ones, PIM governs the policies around those critical identities, and IGA ensures everything is administered correctly and remains compliant. Can you truly achieve fortress-like security by deploying isolated systems, or is a unified, intelligent defense the only sustainable path?
Risks, trade-offs, and blind spots
While the combined power of IAM, PAM, PIM, and IGA offers a robust defense, implementing and maintaining these complex frameworks comes with its own set of risks, trade-offs, and potential blind spots. Acknowledging these challenges is crucial for a successful and sustainable security strategy, preventing the illusion of security from masking underlying vulnerabilities.
One significant risk is over-complexity. Implementing multiple sophisticated security tools, each with its own configurations and integration requirements, can lead to an unwieldy system that is difficult to manage. This complexity can inadvertently introduce new vulnerabilities or create integration challenges between disparate systems, leading to security gaps. A related pitfall is a false sense of security, where organizations believe they are fully protected simply because they have these systems in place, neglecting the crucial aspect of proper implementation, continuous monitoring, and ongoing policy refinement. Tools alone are not a guarantee of security; their effective use is paramount. Even with the best tools, what happens if your implementation is flawed or your team lacks the expertise to maintain it?
The cost of deployment and maintenance for these advanced identity and access management solutions can be substantial, encompassing not just software licenses but also implementation services, ongoing training, and dedicated personnel. Organizations must carefully consider their budget and resource allocation to avoid unforeseen expenses or projects that run over time and budget. There's also a potential impact on user experience, particularly with stringent controls like frequent MFA prompts. While necessary for security, a poorly designed user experience can lead to user frustration, workarounds, or resistance, undermining the effectiveness of the security measures. For organizations relying on specific SaaS platforms, understanding the security implications and configuration nuances, similar to the depth required for a complete guide to SaaS accounting services, is essential to mitigate hidden risks.
Finally, a pervasive blind spot is the lack of skilled personnel. These systems require specialized knowledge to configure, manage, and optimize. A shortage of in-house cybersecurity talent capable of handling the intricacies of IAM, PAM, and IGA can lead to inefficient operations, unaddressed vulnerabilities, and a failure to fully utilize the capabilities of the deployed solutions. This emphasizes that these frameworks are not "set it and forget it" solutions; they demand continuous effort, specialized expertise, and a dedicated team to ensure they remain effective against an ever-evolving threat landscape.
Main points
- IAM: The Broad Foundation: Identity and Access Management (IAM) manages all digital identities, controlling basic authentication and authorization for all users and systems across an organization.
- PAM: Elevated Control for Critical Assets: Privileged Access Management (PAM) is a specialized subset of IAM focused on securing, monitoring, and managing high-risk privileged accounts with advanced controls like password vaulting and just-in-time access.
- IGA & PIM: The Governance Layers: Identity Governance and Administration (IGA) provides the overarching framework for automated identity and access lifecycle management, ensuring compliance and risk reduction through access reviews and SoD. Privilege Identity Management (PIM) complements PAM by focusing on the strategic governance and policy for all privileged identities.
- Symbiotic Relationship: These frameworks are not isolated; they form interlocking layers of defense where IAM establishes identities, PAM secures the critical ones, PIM governs privileged policies, and IGA orchestrates and audits the entire process.
- Tangible Benefits: Implementing these solutions leads to reduced risk of breaches, improved regulatory compliance, enhanced operational efficiency, and creates high-demand skills for cybersecurity professionals.
- Acknowledge Challenges: Be aware of risks such as over-complexity, the potential for a false sense of security, significant costs, impacts on user experience, and the critical need for skilled personnel.
- Continuous Vigilance: Effective identity and access management is an ongoing process requiring continuous effort, refinement, and adaptation to new threats and technologies.
It's time to critically assess your organization's current access management strategy. Invest in the right solutions, deepen your team's knowledge, and build a unified, intelligent defense that truly safeguards your digital future.

